Consulente per la sicurezza delle applicazioni
+7 anni di esperienza nel campo della sicurezza. CTF player, cacciatore di bug e appassionato di sicurezza informatica.

Security activities can not be left until end of development

Vulnerabilities lead to increase in cost and time

Increased in complexity in recent software. Largerly “assembled”
Protecting sensitive data. Mitigating insider threats and solid regulation compliance
Insecure designing can lead to deadlocks. Impossible to fix bugs

Dev and security teams need to collaborate regularly
Lack security skills/knowledge during all stages of development
Security activities are usually not adapted in agile methodologies
Security activities can not be left until end of development

Vulnerabilities lead to increase in cost and time

Increased in complexity in recent software. Largerly “assembled”
Protecting sensitive data. Mitigating insider threats and solid regulation compliance
Insecure designing can lead to deadlocks. Impossible to fix bugs

Dev and security teams need to collaborate regularly
Lack security skills/knowledge during all stages of development
Security activities are usually not adapted in agile methodologies
Let’s take a step back
Failing to firmly prioritize software security can lead to serious consequences
Lack of understanding
Cost
Time constraint
Prioritization of features over security

Perception of invincibility
Let’s take a step back
Failing to firmly prioritize software security can lead to serious consequences
Lack of understanding
Cost
Time constraint
Prioritization of features over security
Perception of invincibility


Rapid, cost-effective software delivery
In a non-DevSecOps envirnoments security issues can easily be both time and cost consuming.
Improved, proactive security
Cybersecurity issues are address as soon as they are identified. In all SDLC/stages. Before aditional dependencies are used, placed, or coded.
Accelerated security vulnerability patching
The ability to identify and patch common vulnerabilities and exposures Common Vulnerabilities Exposures. (CVE) is diminished.
Automation compatible with modern development
Can be integrated into an automated test suite for operations teams if an organization uses a CI/CD pipeline to ship their software.
A repeatable and adaptive process
A mature implementation of DevSecOps ensures consistent security across changing environments and requirements. Resulting in a solid automation, configuration management, orchestration, containers, immutable infrastructure, and even serverless compute environments.
Rapid, cost-effective software delivery
In a non-DevSecOps envirnoments security issues can easily be both time and cost consuming.
Improved, proactive security
Cybersecurity issues are address as soon as they are identified. In all SDLC/stages. Before aditional dependencies are used, placed, or coded.
Accelerated security vulnerability patching
The ability to identify and patch common vulnerabilities and exposures Common Vulnerabilities Exposures. (CVE) is diminished.
Automation compatible with modern development
Can be integrated into an automated test suite for operations teams if an organization uses a CI/CD pipeline to ship their software.
A repeatable and adaptive process
A mature implementation of DevSecOps ensures consistent security across changing environments and requirements. Resulting in a solid automation, configuration management, orchestration, containers, immutable infrastructure, and even serverless compute environments
Relationship lies in their shared goals
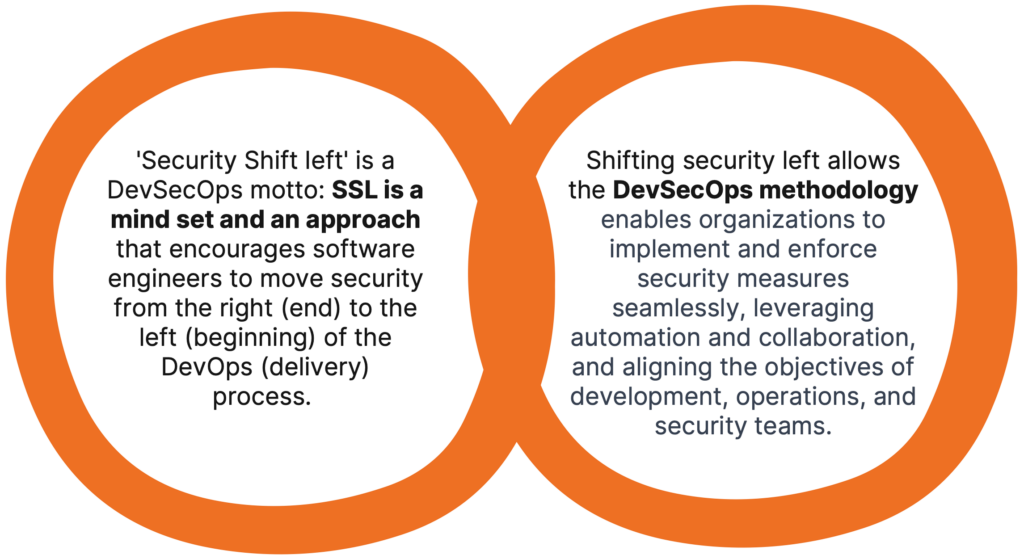
Relationship lies in their shared goals

How we shift security to the left
Educational-level
Developers’ security self-assessment
Knowledge-level
AppSec design
Implementation-level
Security tools consultancy
Culture-level
Stakeholders’ security awareness
How we shift security to the left
Educational-level
Developers’ security self-assessment
Knowledge-level
AppSec design
Implementation-level
Security tools consultancy
Culture-level
Stakeholders’ security awareness
Areas and field of focus
Areas and field of focus

Consulente per la sicurezza delle applicazioni
+7 anni di esperienza nel campo della sicurezza. CTF player, cacciatore di bug e appassionato di sicurezza informatica.



Manifestation of success
Secure Design and Culture
Threat Modelling
Secure Implementation
Secure Verification
Production Security Monitoring
Incident Management
Manifestation of success
Secure Design and Culture
Threat Modelling
Secure Implementation
Secure Verification
Production Security Monitoring
Incident Management
Delivered by: SORINTians
Introduce Shift Security Left
Client is developing a critical software app. Requirements included:
In a proposal form.
Result & delivery (UTD)
Delivered by: SORINTians
Introduce Shift Security Left
Client is developing a critical software app. Requirements included:
In a proposal form.
Result & delivery (UTD)
Enhance the CI/CD Practice
Result & delivery (UTD)
Migration and major changes in the CI/CD tools
Result & delivery (UTD)





Welisten
24x7x365
Welisten
24x7x365
